Azure Webhook Receiver
The Azure webhook receiver responds to push and ping events originating
from Azure Container Registry repositories and git.push events originating
from Azure DevOps repositories.
The receiver unconditionally responds to ping events with an HTTP 200 status
code.
The receiver responds to push and git.push events by refreshing all
Warehouse resources subscribed to the repositories that correspond to the
event.
"Refreshing" a Warehouse resource means enqueuing it for immediate
reconciliation by the Kargo controller, which will execute the discovery of new
artifacts from all repositories to which that Warehouse subscribes.
Configuring the Receiver
An Azure webhook receiver must reference a Kubernetes Secret resource with a
secret key in its data map.
This secret will not be shared directly with Azure.
Azure does not natively implement any mechanism whereby receivers may authenticate inbound webhook requests. To compensate for this, Kargo incorporates the secret into the generation of a hard-to-guess URL for the receiver. This URL serves as a de facto shared secret and authentication mechanism.
The following commands are suggested for generating and base64-encoding a complex secret:
secret=$(openssl rand -base64 48 | tr -d '=+/' | head -c 32)
echo "Secret: $secret"
echo "Encoded secret: $(echo -n $secret | base64)"
apiVersion: v1
kind: Secret
metadata:
name: azure-wh-secret
namespace: kargo-demo
labels:
kargo.akuity.io/cred-type: generic
data:
secret: <base64-encoded secret>
---
apiVersion: kargo.akuity.io/v1alpha1
kind: ProjectConfig
metadata:
name: kargo-demo
namespace: kargo-demo
spec:
webhookReceivers:
- name: azure-wh-receiver
azure:
secretRef:
name: azure-wh-secret
Retrieving the Receiver's URL
Kargo will generate a hard-to-guess URL from the receiver's configuration. This URL can be obtained using a command such as the following:
kubectl get projectconfigs kargo-demo \
-n kargo-demo \
-o=jsonpath='{.status.webhookReceivers}'
Registering with Azure
The Azure webhook receiver supports both Azure Container Registry and Azure DevOps services.
Azure Container Registry
-
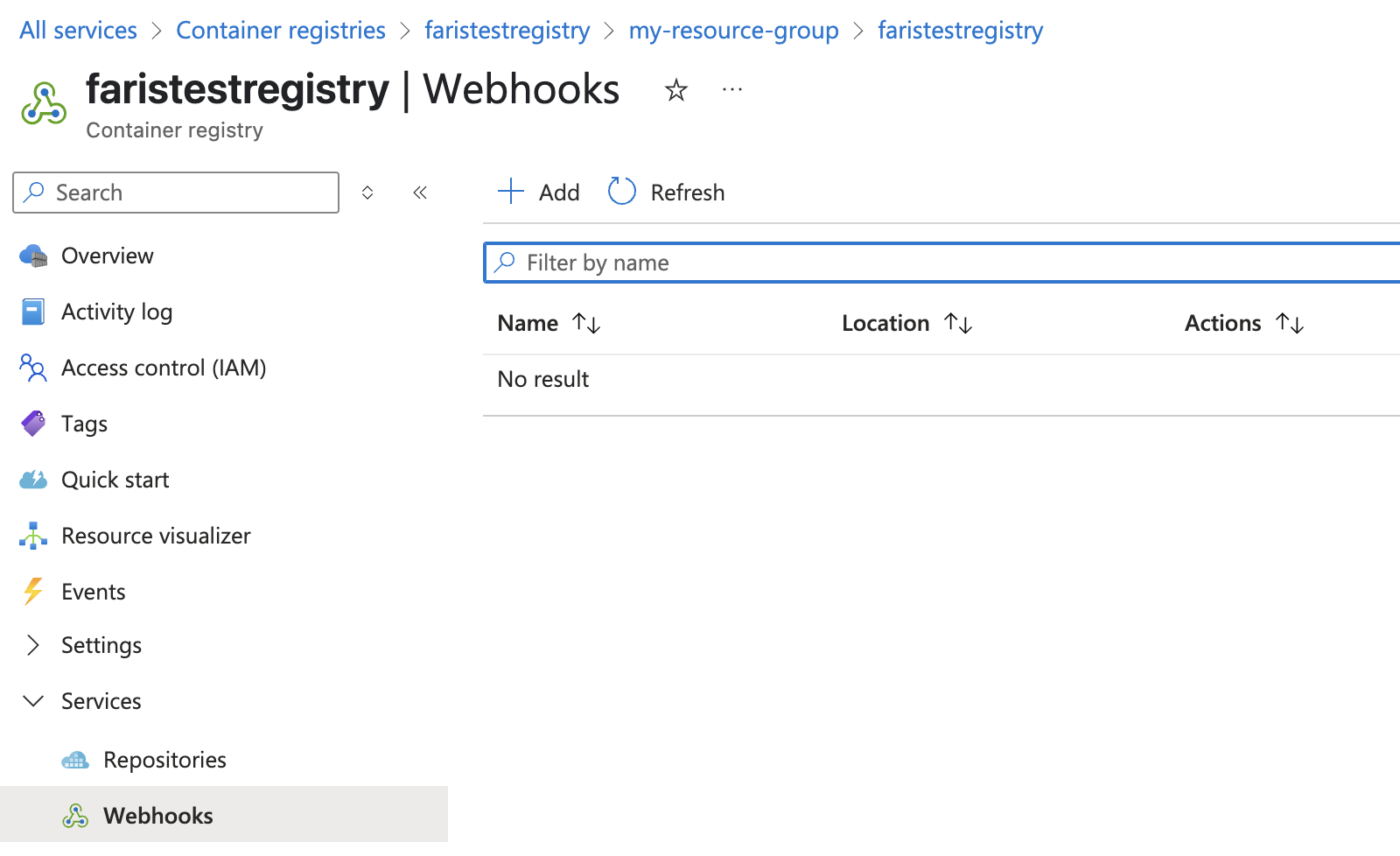
In your Azure Container Registry portal, on the left-hand side, navigate to Services → Webhooks.
-
At the top of the screen, click Add.
-
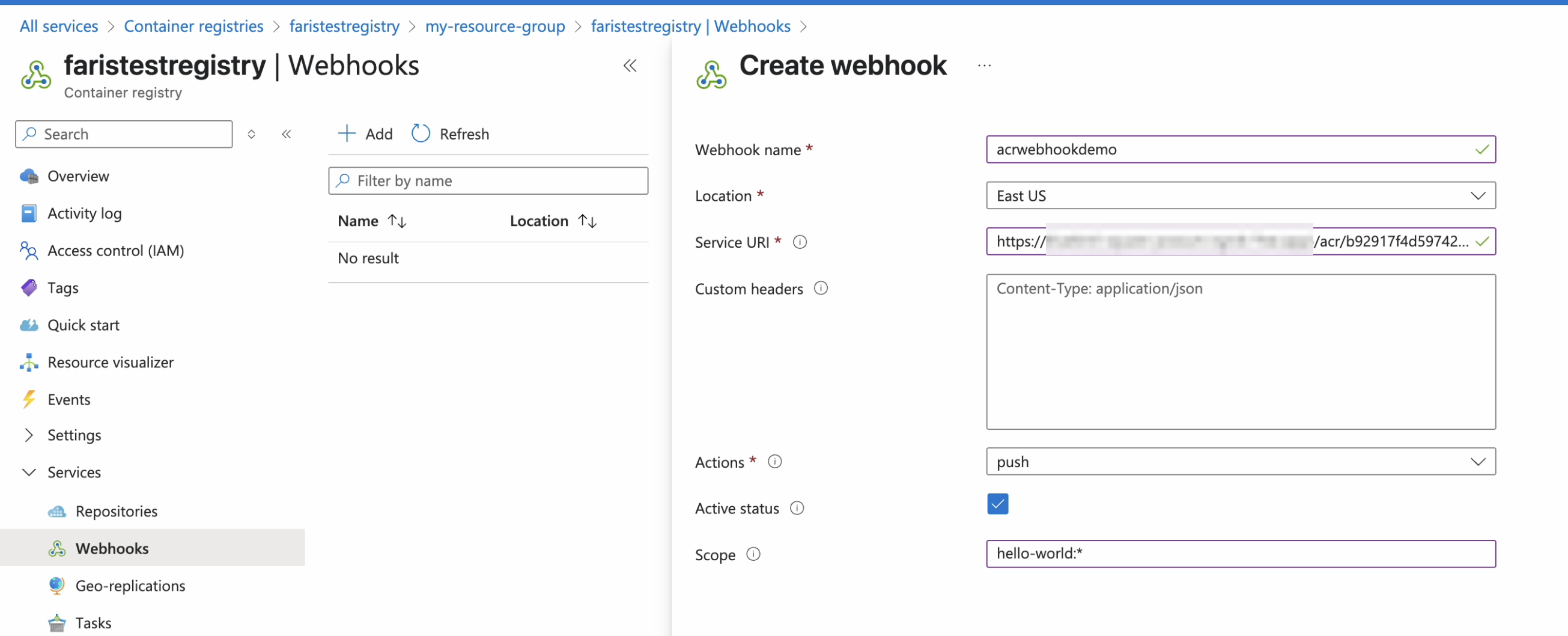
Complete the Create webhook form:
-
Enter a descriptive name in the Webhook name field.
-
Select the Location closest to where your Kargo instance is running.
-
Complete the Service URI field using the URL for the webhook receiver.
-
From the Actions drop-down menu, select
push. -
Ensure Active is checked.
-
Set the Scope using the format
<repository>:<tag>.noteWildcards are supported in both the
repositoryandtagpart of the Scope string. -
Click Create.
-
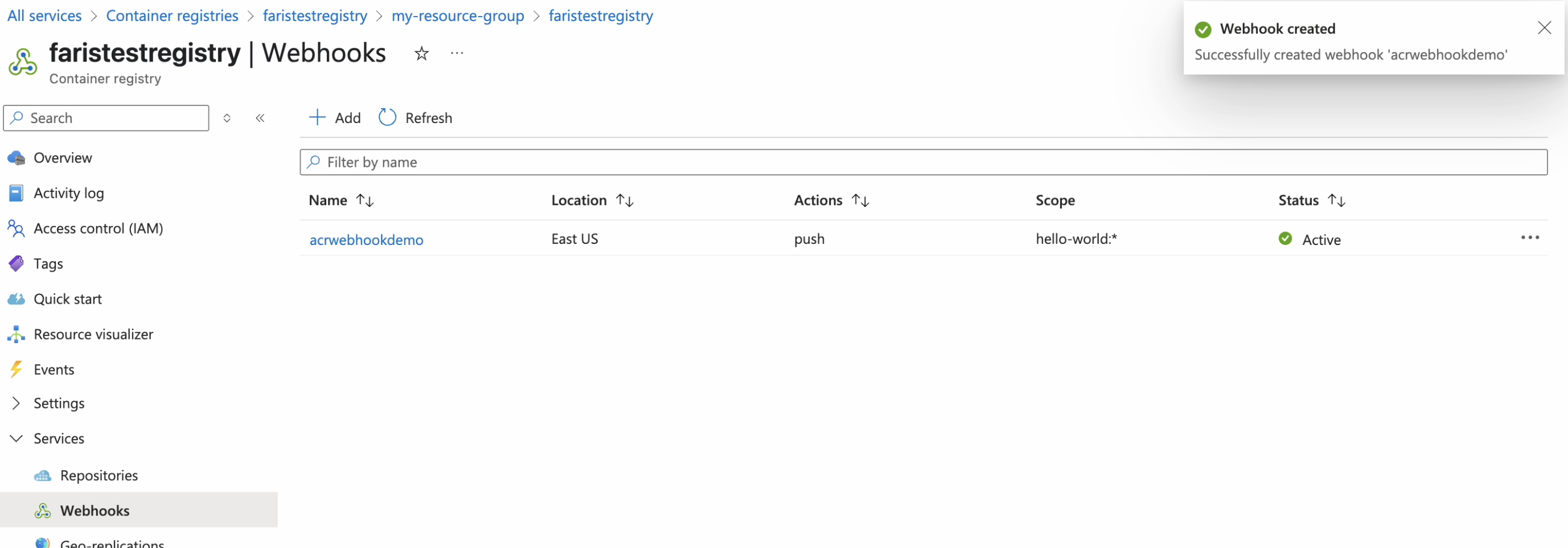
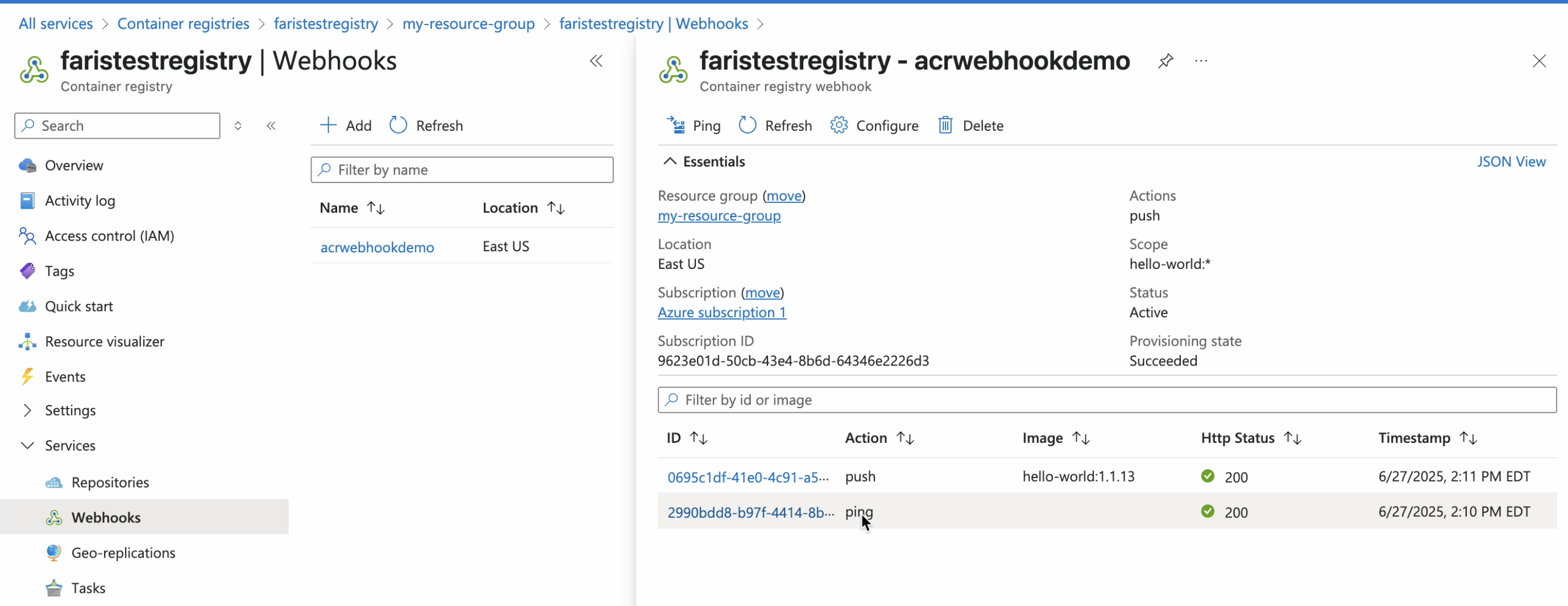
Return to the Webhooks dashboard and select the newly created webhook.
-
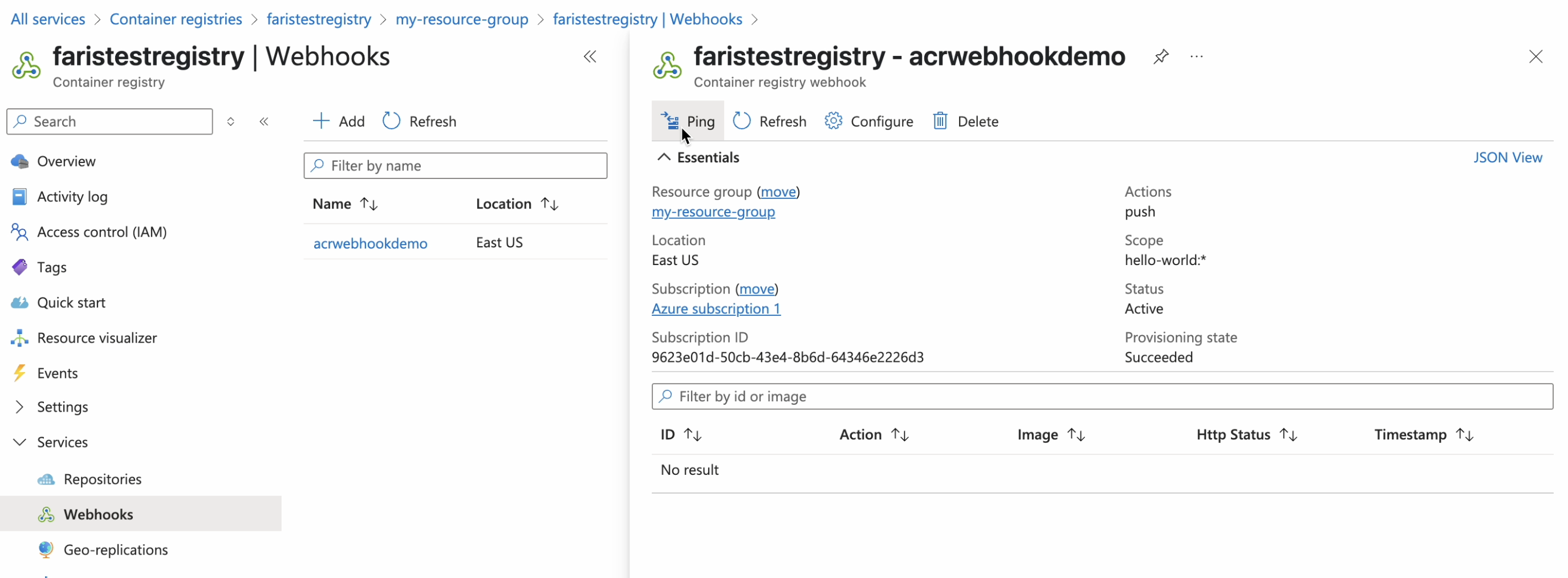
Click Ping.
-
Click Refresh.
-
Confirm a 200 Http Status for the Ping action.
-
For additional information on configuring ACR webhooks, refer directly to the ACR Docs.
Azure DevOps
-
Navigate to
https://dev.azure.com/<org>/<project>/_settings/serviceHooks, where<org>has been replaced with an organization name and<project>has been replaced with the name of a project belonging to that account and for which you are an administrator. -
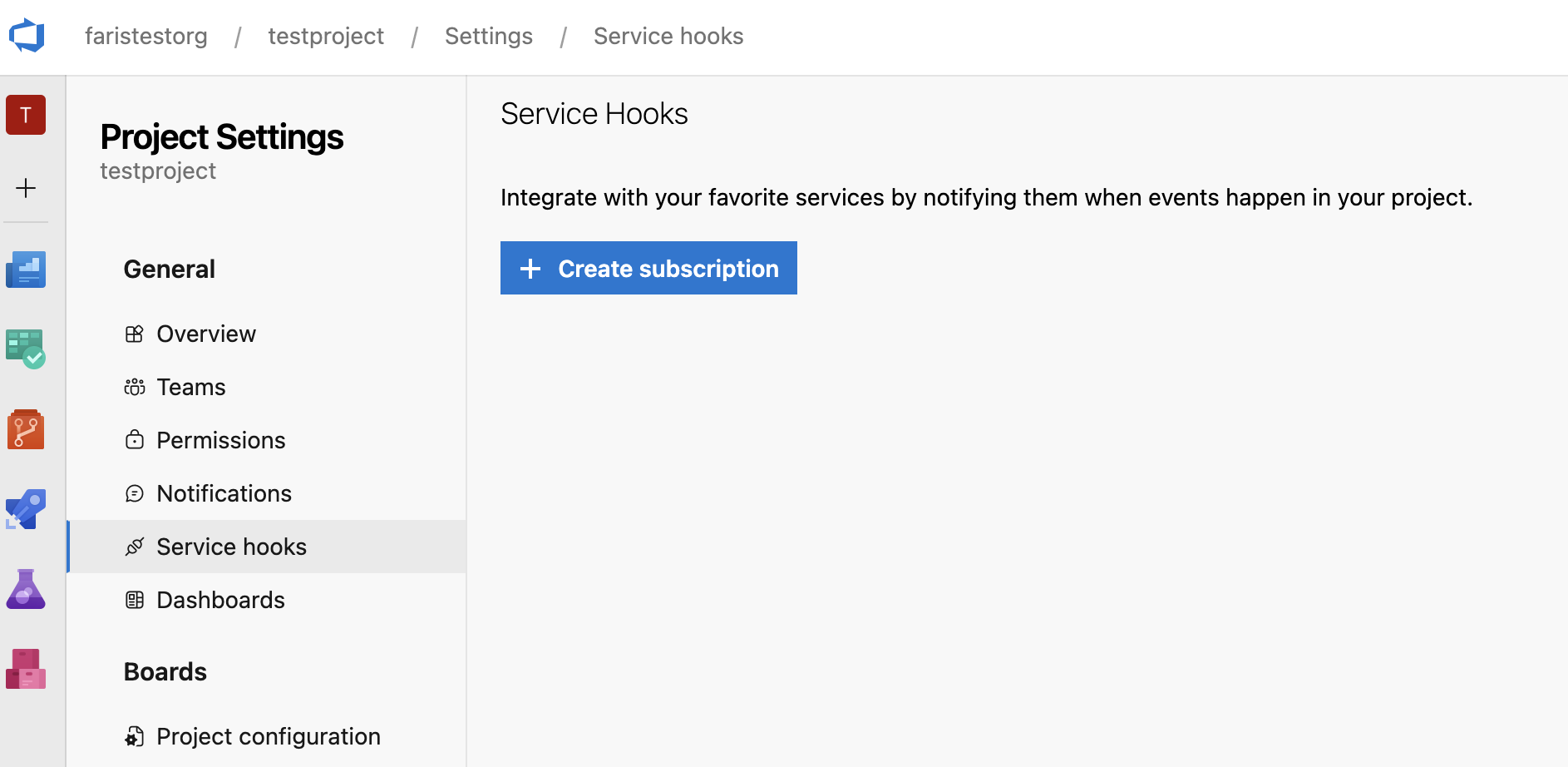
On the left-hand-side menu under General, click Service Hooks.
-
Click Create Subscription.
-
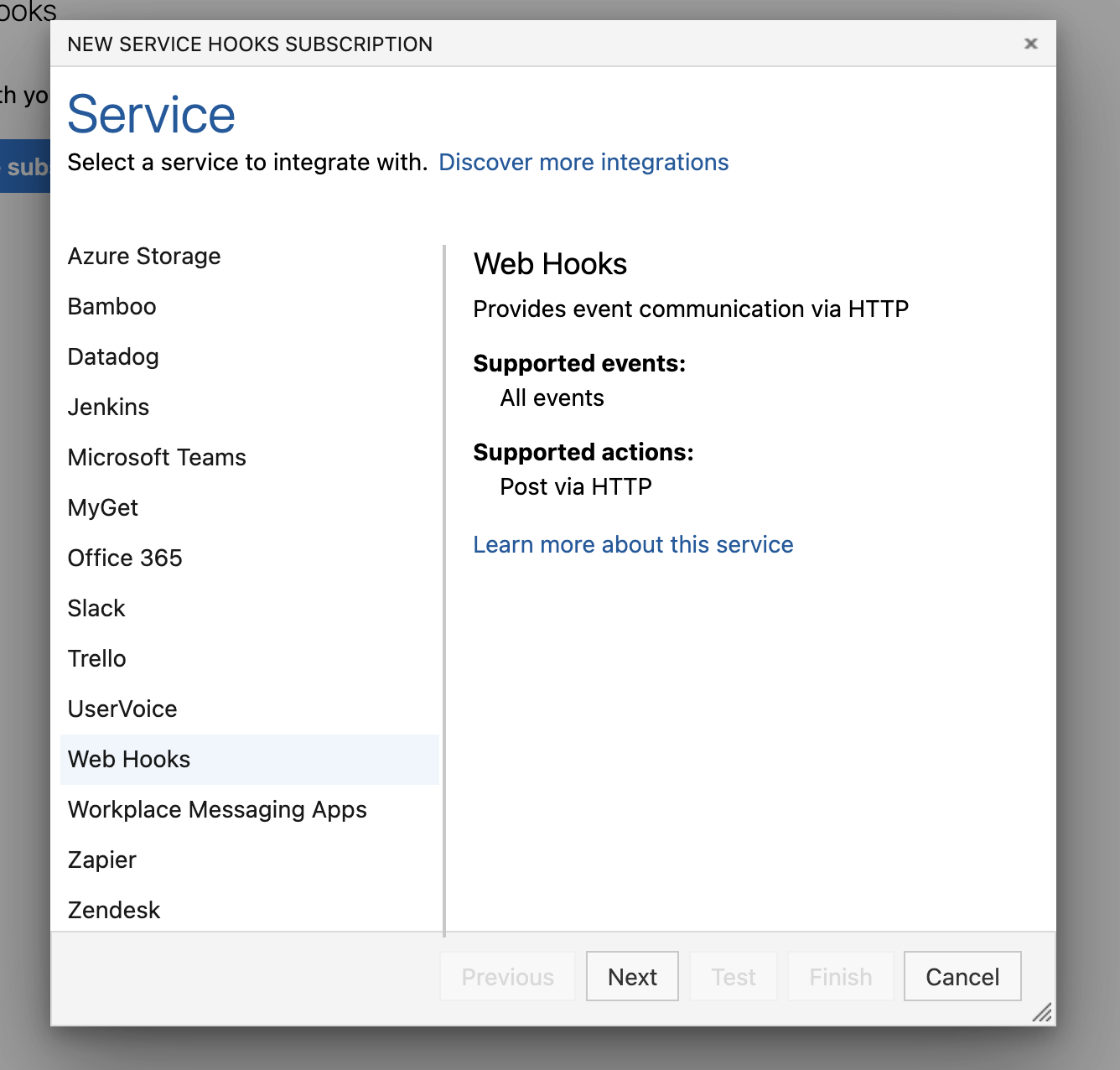
In the New Service Hooks Subscription modal, scroll down to Webhooks on the left-hand-side.
-
Click Webhooks.
-
Click Next.
-
Complete the Trigger form:
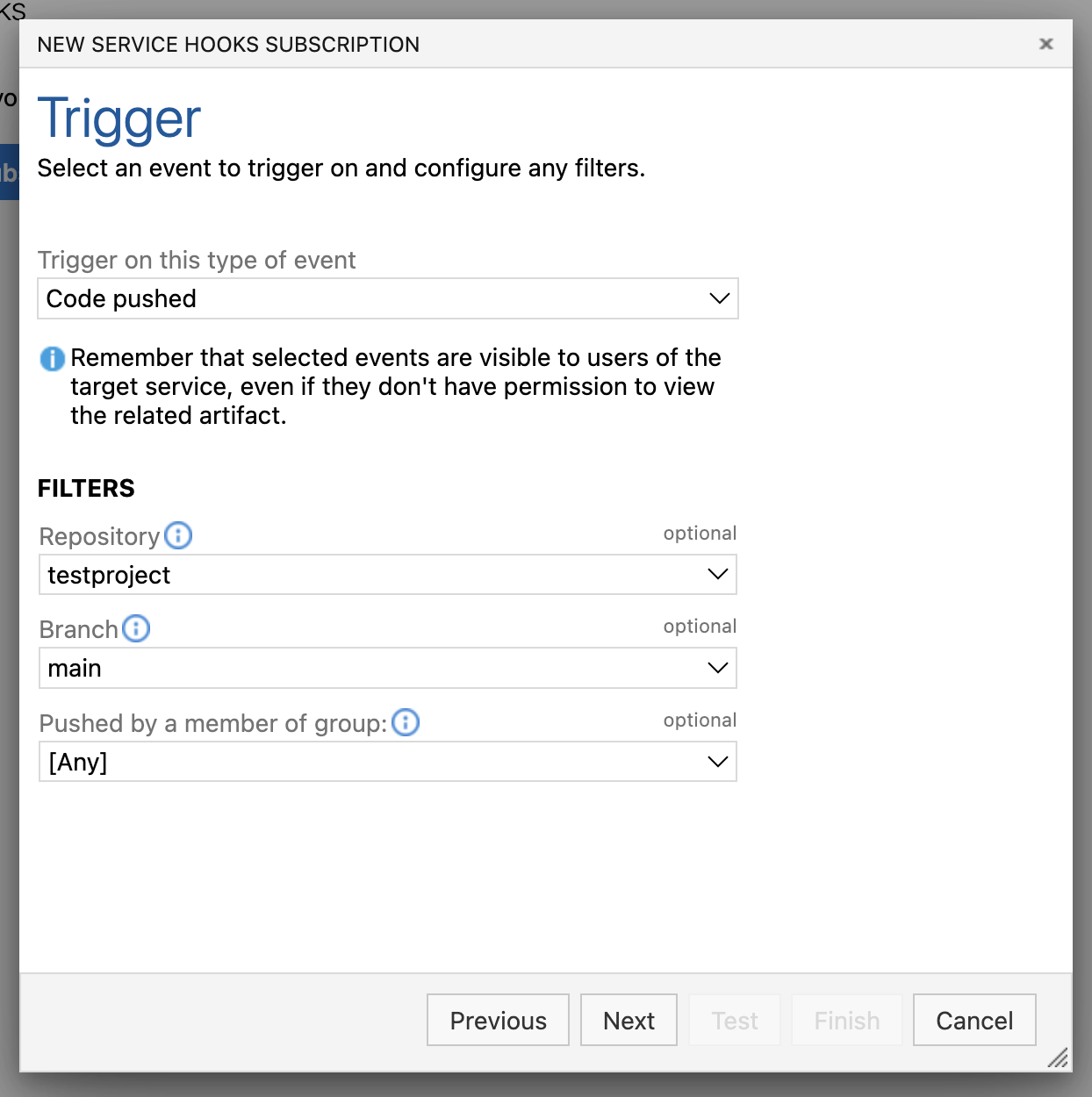
-
Select Code Pushed from the drop-down menu labeled Trigger on this type of event.
-
Select the Repositories, Branches, and Users for which the event will trigger for.
-
Click Next.
-
-
Complete the Action form:
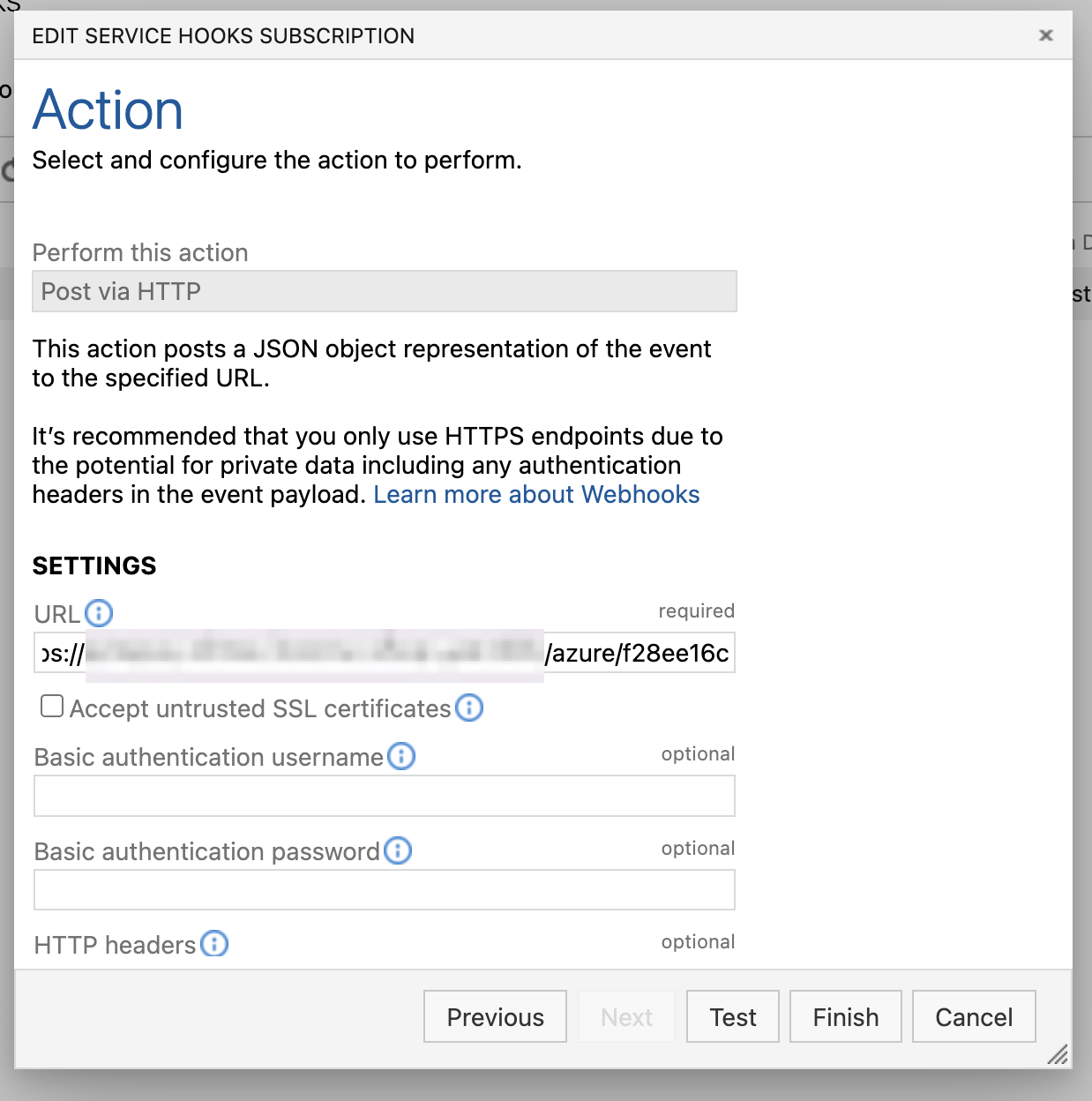
-
Complete the Service URI field using the URL for the webhook receiver.
-
Click Test.
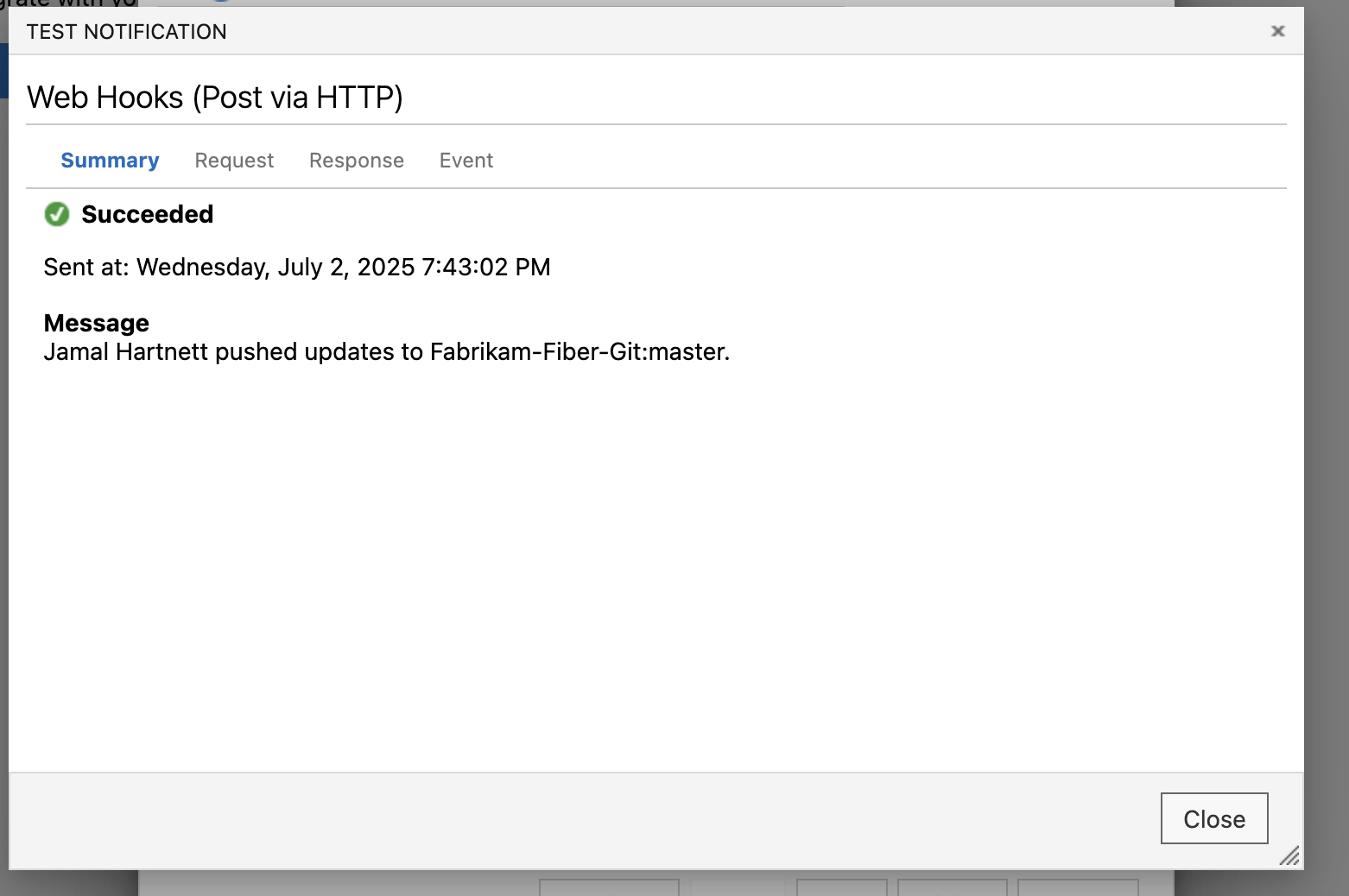
-
-
After receiving a Succeeded notification, click Close.
-
Click Finish.
For additional information on configuring Azure DevOps webhooks, refer directly to the Azure DevOps Docs.